#Microsoft’s Project Freta is intended to stop malware in Azure
“#Microsoft’s Project Freta is intended to stop malware in Azure”
RECOMMENDED: Click here to fix Windows errors and optimize system performance

As the Project Freta comes from Microsoft Research, the company classifies it as a ‘technology demonstration’.
It captures a snapshot of a VM (supports Hyper-V and VMWare), and then inspects its contents for malware existence. To achieve this functionality, the user should sign in on the Project Freta web site and then submit VM images used in the special Azure region.
The official announcement says:
The Project Freta analysis engine consumes snapshots of whole-system Linux volatile memory and extracts an enumeration of system objects. Some kernel hooking identification is performed automatically; this can be used by analysts to detect novel rootkits. The analysis portal is available in prototype form for public use: https://freta.azurewebsites.net.
The prototype portal supports many types of memory snapshots as inputs. Currently, only a Hyper-V checkpoint has been evaluated to provide a reasonable approximation of the “element of surprise” necessary to achieve trusted sensing:
- Use the Hyper-V checkpoint feature to produce a VMRS file
- Convert a VMWare snapshot to produce a CORE file
- Extract memory from within a running system using AVML
- Extract memory from within a running system using LiME
Memory snapshots for a running VM in Azure can be taken with a special sensor that will allow to capture and move instance’s memory to an offline area for analysis without stopping its execution.
Completed in the winter of 2019, this sensor capability is currently only available to Microsoft researchers and is not fielded to any of Microsoft’s commercial clouds—executive briefings and demos are available. This sensor, coupled with the Freta analysis environment, demonstrates a path to cheap, automated memory forensic audits of large enterprises (10,000 VMs).
When analysis is complete, Project Freta will create a report. The report data can be also obtained via REST API and Python.
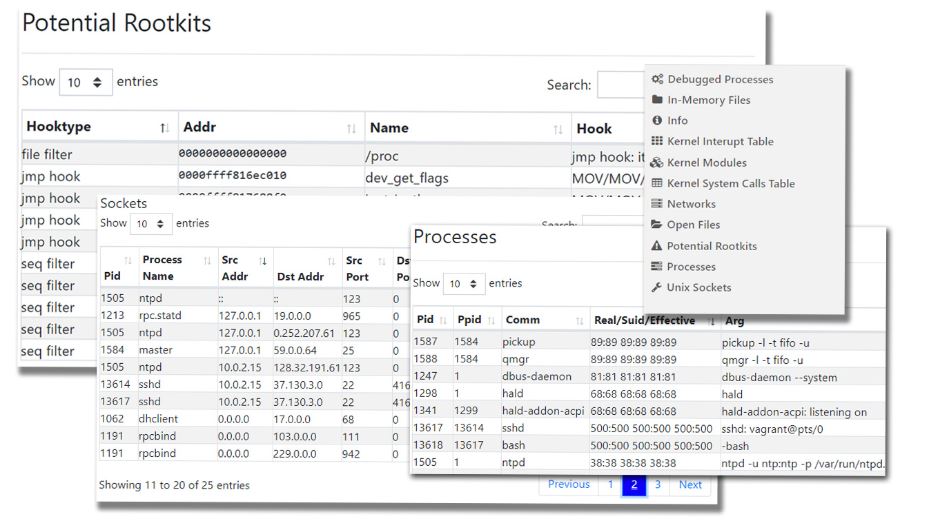
The report contains an enumeration of system objects over the interval during which the sample was taken:
- Global values and addresses
- Debugged processes
- In-memory files
- Kernel interrupt table
- Kernel modules
- Kernel syscall table
- Networks
- Open files
- ARP table (arp)
- Open sockets
- Processes
- Unix sockets (lsof)
RECOMMENDED: Click here to fix Windows errors and optimize system performance
If you want to read more like this article, you can visit our Technology category.
if you want to watch Movies or Tv Shows go to Dizi.BuradaBiliyorum.Com for forums sites go to Forum.BuradaBiliyorum.Com



