#How Safe Is Two Factor Authentication Exactly? – Review Geek
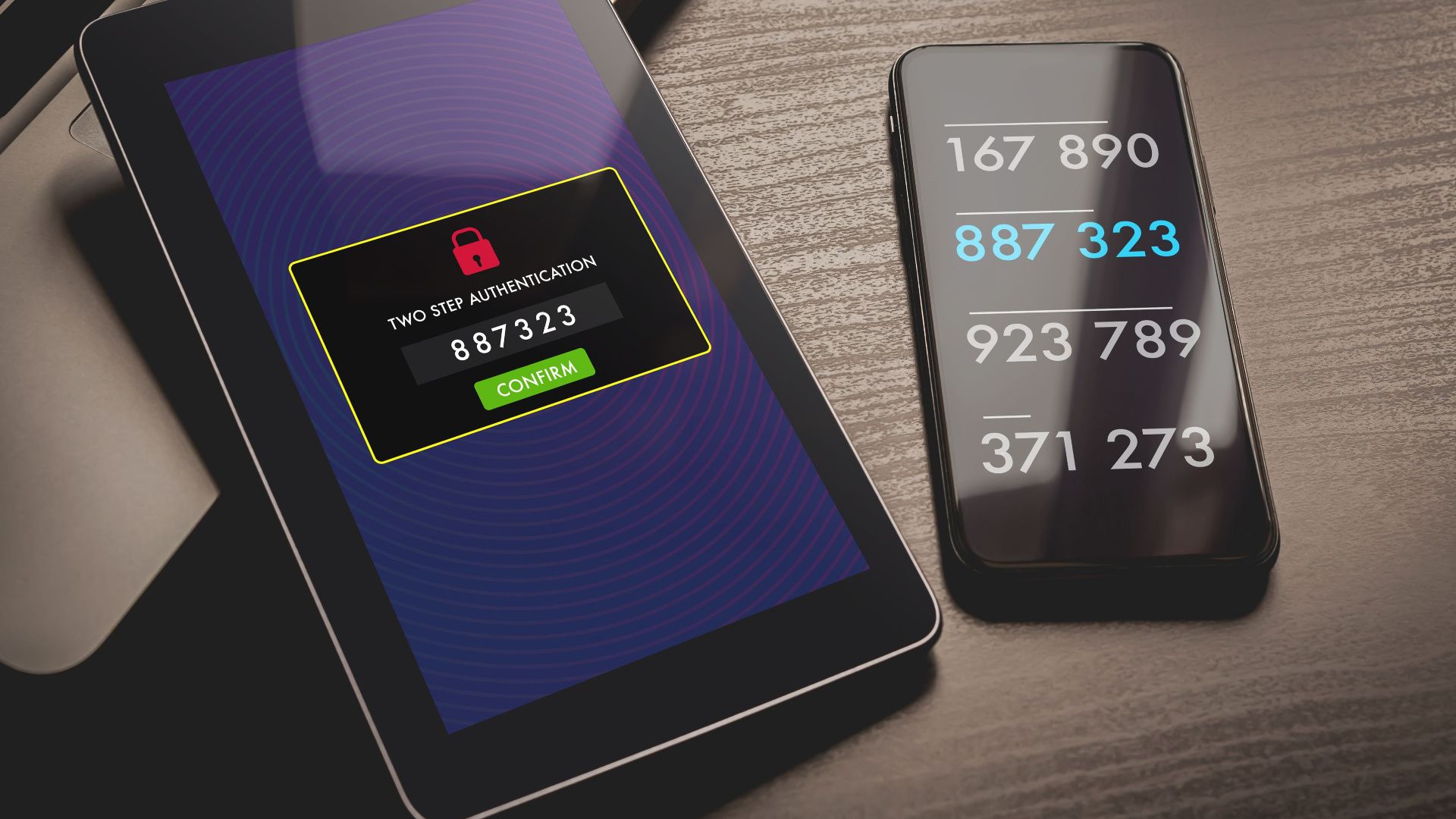
Table of Contents
“How Safe Is Two Factor Authentication Exactly? – Review Geek”

Two-factor authentication (2FA) is becoming mandatory on many websites, and it’s easy to see why. On the face of it, requiring you to confirm your login via SMS or an app provides a solid second layer of security. But just how strong is it?
With security threats on the rise, and people having more than ever to lose online, it’s only natural to want to protect yourself as much as possible. While having a social media account hacked may be annoying, there are far more serious consequences to having lax cyber security. Hackers could access your bank accounts and drain your savings, sensitive files and pictures could be stolen, and you could even have a work account hacked and land in hot water with your boss.
The term “two-factor authentication” refers to a second step to confirm who you are. An additional layer of protection will, by default, provide more security than a single barrier. However, there is more than one method of 2FA; all methods offer different levels of security, and some are more popular than others. So, can 2FA make your sensitive accounts invulnerable to hackers? Or is it just a huge waste of effort? Let’s find out.
SMS is Not as Safe as It Seems

The most common form of 2FA is SMS based. Your bank, social media account, or email provider sends you a text message with a code, which you enter within a set time period. This gives you access to the account and keeps your login safe from anyone who doesn’t have your phone. On the face of it, this is the most secure method. Someone would need to steal your cellphone or devise some elaborate, James Bond-esque way of cloning your SIM card to get around this one, right? Wrong.
Last year Vice claimed a hacker could use a flaw in the SMS system to hijack your number and reroute your SMS messages for as little as $16. There are also more and less sophisticated methods an individual can use to access your messages. The simplest involves simply calling your phone company claiming to be you, saying your phone is missing, and asking the company to switch your number to another sim card. More complex ones involve attacking the company directly and intercepting messages.
As for how they get personal details and your phone number? They could do some shady deals and buy personal information on you and your various online activities over the dark web. Or they could check your Facebook for details like your date of birth, phone number, schools you attended, and your mother’s maiden name. You may know precisely what information you put online, but many people don’t.
At the very least, it is possible to protect yourself from sim-swapping attacks or be alerted when they occur. But you should consider adopting a different 2FA method if possible.
Email-Based 2FA Could Be Pointless
Two-factor authentication should add an extra layer of security between your account and a potential threat. However, if you’re lazy, all you’re doing is adding an extra step and potentially giving an internet miscreant a good laugh. If you’re the sort of person who uses the same password for everything and their email account is being used to secure their target account, you could be in a lot of trouble. A hacker can log into that email address using the same details he’s already stolen and authenticate his actions.
If you insist on using email-based 2FA, you should make a separate email account purely for authentication purposes with its unique and difficult-to-crack password. Alternatively, use another method because they’re all more secure.
Push-Based Could Let You Down

Push-based authentication can be quick, easy, and secure. A device, which can be your smartphone, is linked with your account and registered as your 2FA method of choice. From this point on, whenever you want to sign in, you’ll receive a push notification on that device. Unlock your phone, confirm it’s you, and you’re in. Sounds perfect, right?
Unfortunately, there is a catch or two. The main problem with the push-based method is your device needs to be online for you to use it. If you need to access an account and your phone is struggling to get a signal, you’re out of luck. It’s worth pointing out that this hasn’t been an issue for me in the few years I’ve used it. If I need to log in, I’m usually somewhere with WiFi, which my phone can use. I’m more likely to be somewhere where I can’t receive an SMS than somewhere where I’m trying to log in and unable to get a push notification sent to my phone.
Hardware-Based 2FA is A Lot of Effort

There is also the option of having a long, complex, authentication password physically written down. This is a string of numbers and characters and a popular method for securing cryptocurrency wallets. As these are difficult to crack, The FBI broke into a house to find a piece of paper containing a 27-character password, which was easier than working it out. You can’t hack something written on a piece of paper and stored in a desk drawer, and supercomputers can take years to go through the possible combinations involved in high-level encryption.
Of course, if it’s in your desk drawer, it isn’t with you. If you take it with you, you can lose it as easily as you can lose a 2FA USB. And when it’s gone, you’ll need to go through an account recovery process at best or lose access to your account at worst. The physical method is the best thing you can do in terms of security but the worst in terms of convenience. You can use it as a rock-solid account recovery method, but it’s probably best avoided for things you access on the fly.
App-Based 2FA is Worth the Hassle
Downloading an app like Google Authenticator comes with a few benefits. It is more secure than methods like email and SMS authentication; it’s free in most cases and still functions if the device hasn’t got an internet connection. This is because of the timing-based algorithm, which produces different keys at different moments in time. A key is only valid for a set period and should match the device and the site the user is logging into.
There are still some vulnerabilities. With Google Authenticator, there is no lock on the app itself, so anyone who can access your phone can open and use it. Some malware programs could also take advantage of the lack of an access key, so you should consider alternatives like the Microsoft Authenticator app, which adds an extra layer of security to the authentication process with features like biometric unlock. It is also vulnerable to phishing attacks, where you’ll enter the key into a fake website and allow a fast-acting hacker or robot to use it. They are also open to interception.
You Should Still Use 2FA
(I know this is cheesy, and images aren’t my strong point, but this doesn’t feel right without keeping up the “all hackers wear hoodies in dark rooms” trope.)
I have identified flaws with every method mentioned, and more will probably emerge as time goes on. But the more security you have, the better. You should 100% use 2FA and other methods like a password manager to secure your online accounts.
There is a balance between security and convenience, so find what works for you. Maybe the hardware-based method is overkill or something you’re guaranteed to lose. SMS may not be as secure as it seems, but a bit of effort is still required to crack it. If you’re just an average Joe, you’re probably not going to be worth individually targeting, and SMS authentication is something that will massively increase your online security.
Look at your life, assess what you have to lose, and work out how much effort you want to put in. But pick at least one 2FA method (that isn’t email-based) and make sure you have a different password for every account you care about.
If you liked the article, do not forget to share it with your friends. Follow us on Google News too, click on the star and choose us from your favorites.
For forums sites go to Forum.BuradaBiliyorum.Com
If you want to read more like this article, you can visit our Technology category.




